IoT Hacking: Peeking in IPSEC tunnels with Wireshark
IPSEC is often the go-to security measure for IoT devices that must connect back to their home-base for logging, software upgrades, or other communication needs. When doing an initial security survey of a device you'll want access to those tunnels to get a peek at what is being sent between the client device and the service infrastructure.
Wireshark is the de facto tool for network inspection and it has support for decrypting IPSEC tunnels provided that you have recovered the IPSEC encryption parameters and that the encryption algorithms selected during IKE are supported by the Wireshark dissectors.
uh... so what if you don't already have all of that? Answer: Get access to the packets before encryption!
This is possible on Linux based devices provided that you have root access and access to an
infrequently used kernel module called xt_TEE.ko. The xt_TEE module is part of the netfilter
framework and will be available if you have CONFIG_NETFILTER_XT_TARGET_TEE enabled in your kernel. TEE, like
the command line tee command. [1]
xt_TEE provides a new netfilter target that can duplicate and send a copy any network packets that traverse
an iptable and chain. The only real difficulty is understanding where to install the tee.
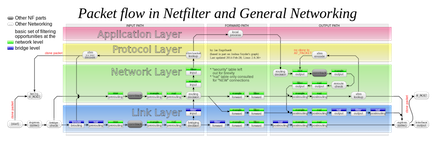
Attribution: Wikimedia Commons
Consult the diagram above to find that there are two spots of interest:
- Outgoing in-the-clear traffic from local processes: Mangle table, post-routing chain
- Incoming in-the-clear traffic for local processes: Mangle table, pre-routing chain
Installing the iptables rules is easy once you know where to put them:
# Captures alice->bob traffic in the clear and redirects to gateway sudo iptables -t mangle -A POSTROUTING -j TEE --gateway 192.168.242.131 -d 192.168.242.130 # Captures bob->alice traffic in the clear and redirects to gateway sudo iptables -t mangle -A PREROUTING -j TEE --gateway 192.168.242.131 -d 192.168.242.128 # List sudo iptables -L -t mangle
In the example above we are copying all traffic intended for .130 and sending a copy of it to .131. By virtue of where the tee has been installed this traffic will be in-the-clear.
To intercept the copied packets capture using Wireshark. You'll observe that the copied packets are identical to the original with the exception that the destination MAC address has been modified.
Done inspecting? Clean up your tables:
# Nuke tables sudo iptables -t mangle -F POSTROUTING sudo iptables -t mangle -F PREROUTING
Using this technique you can quickly access in-the-clear traffic with Wireshark with minimal disruption to the device under observation.
Happy hacking!
[1]: Don't have CONFIG_NETFILTER_XT_TARGET_TEE enabled in your kernel? Don't despair. You can
simply build the module, transfer it to the target, and insmod xt_TEE.ko. You can even do this
without the original kernel source. Mike Hommey walks you through how to do this in his helpful
post "Building a Linux kernel module without the exact kernel headers".